CVE Management
Context
The IT Security team received an alert regarding a new critical vulnerability (CVE) that could have a significant impact on systems. This CVE affects several applications. To prevent potential exploitation of this vulnerability, it is crucial to detect and prevent any new application deployments that may contain it.
Objective of the exercise
The main objective is to implement a security policy that blocks any application deployment containing the identified CVE on the affected cluster. This policy must be automated to prevent any risk of unintentional deployment of a vulnerable application.
Exercise steps
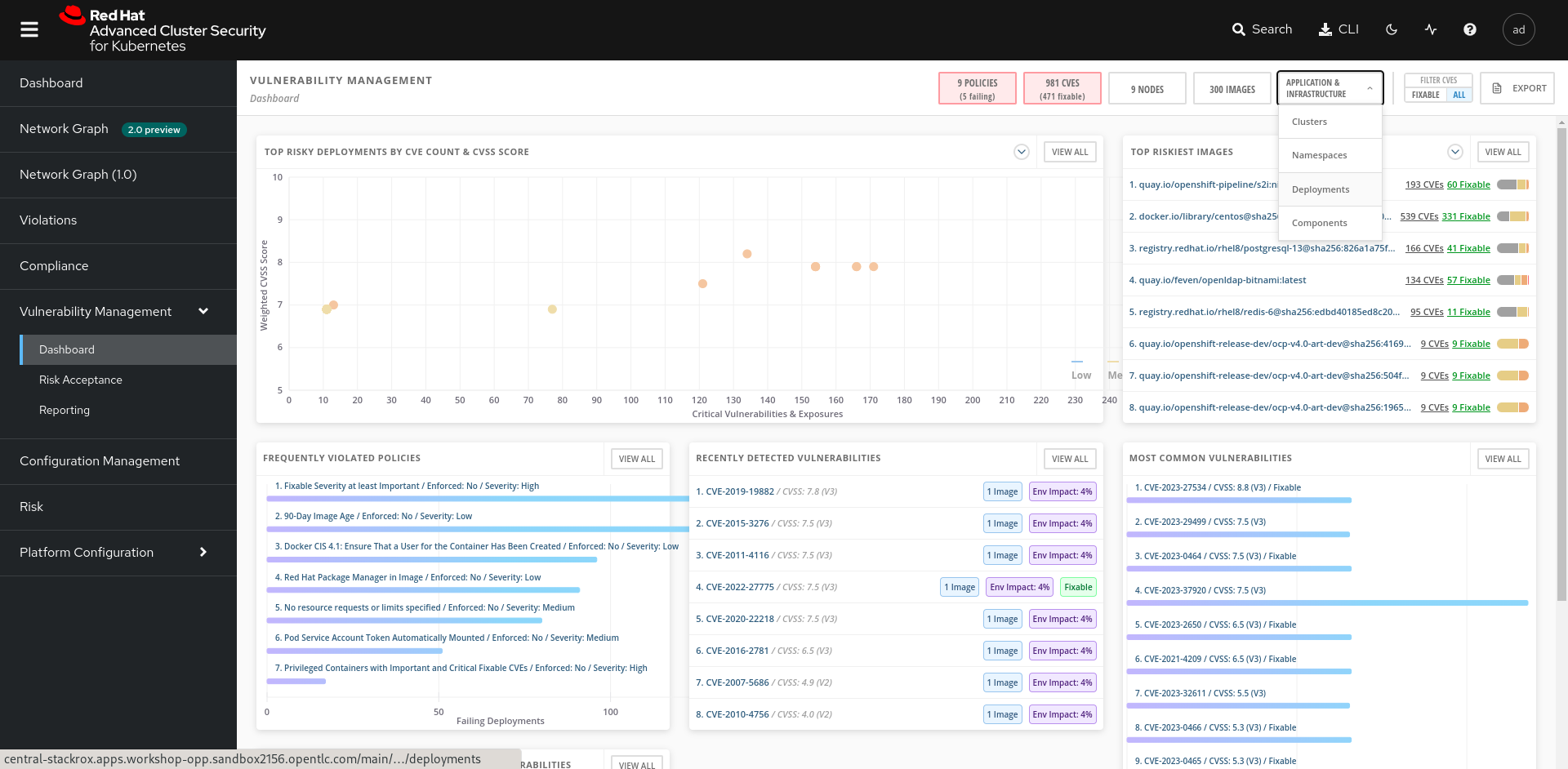
Access the RHACS interface and go to the Vulnerability Management section. This interface gives you visibility over all the images belonging to your scope.
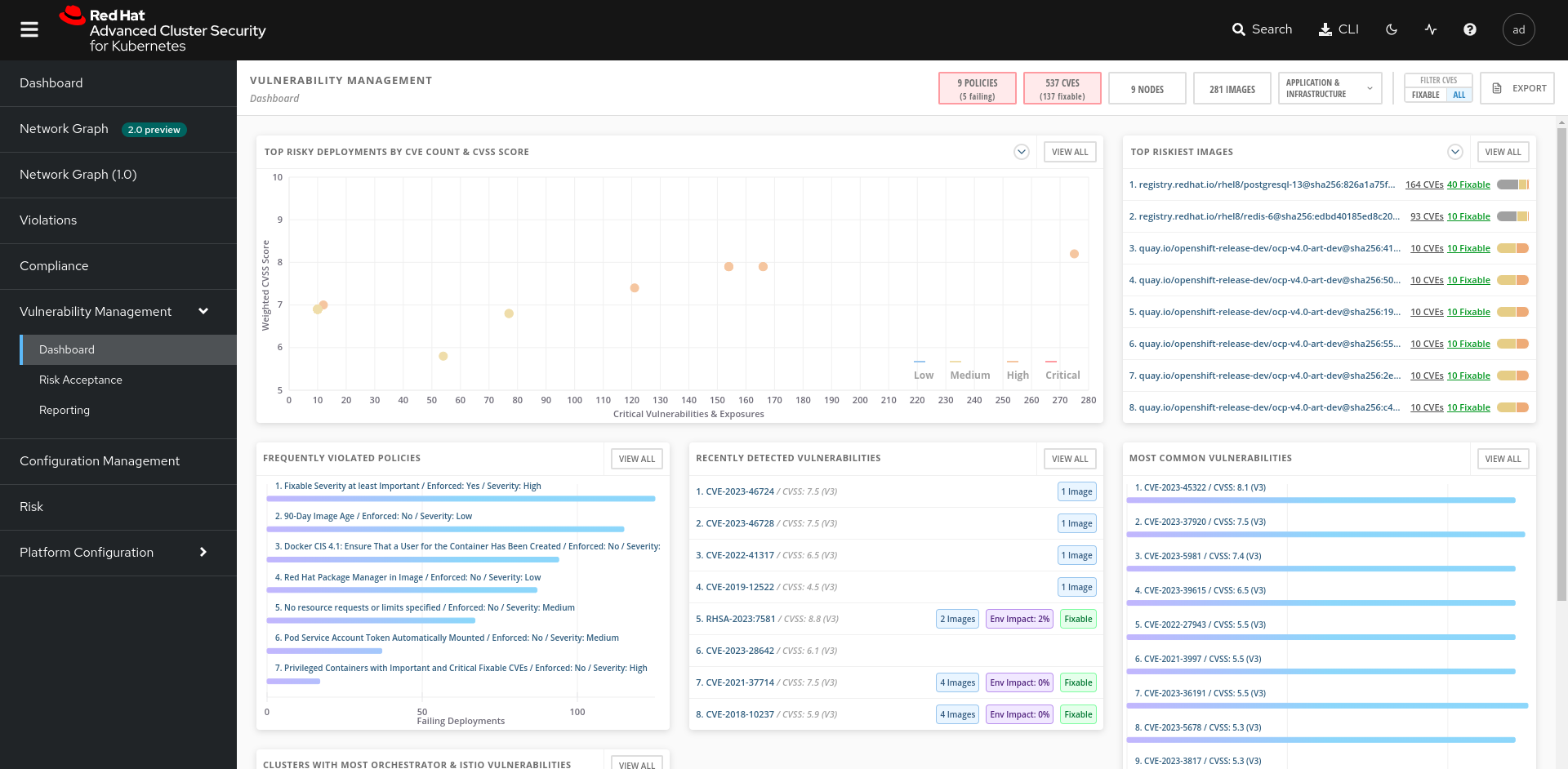
Up to you
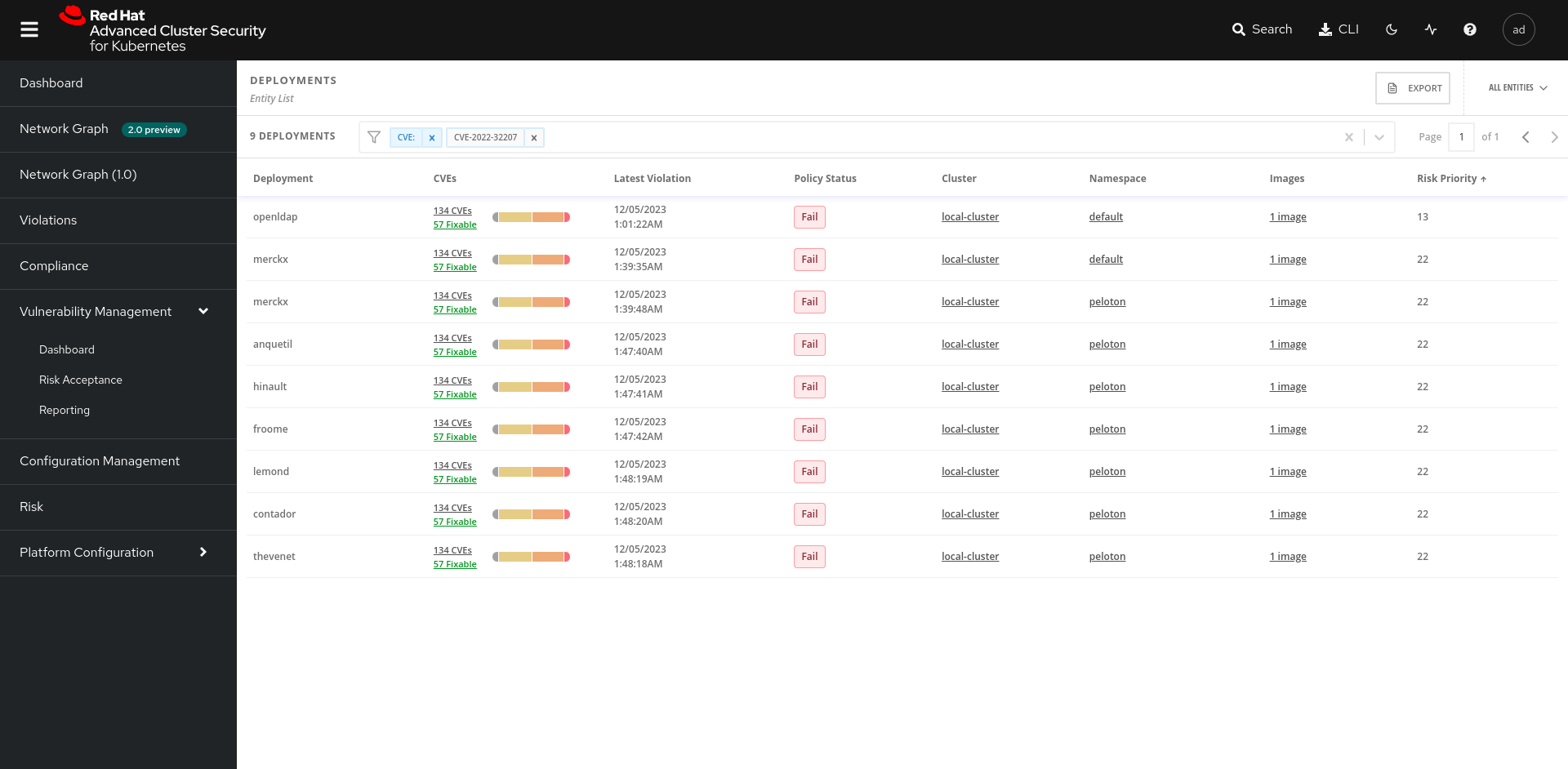
From these different dashboards we ask you to find and export all the deployments affected by CVE in PDF format.
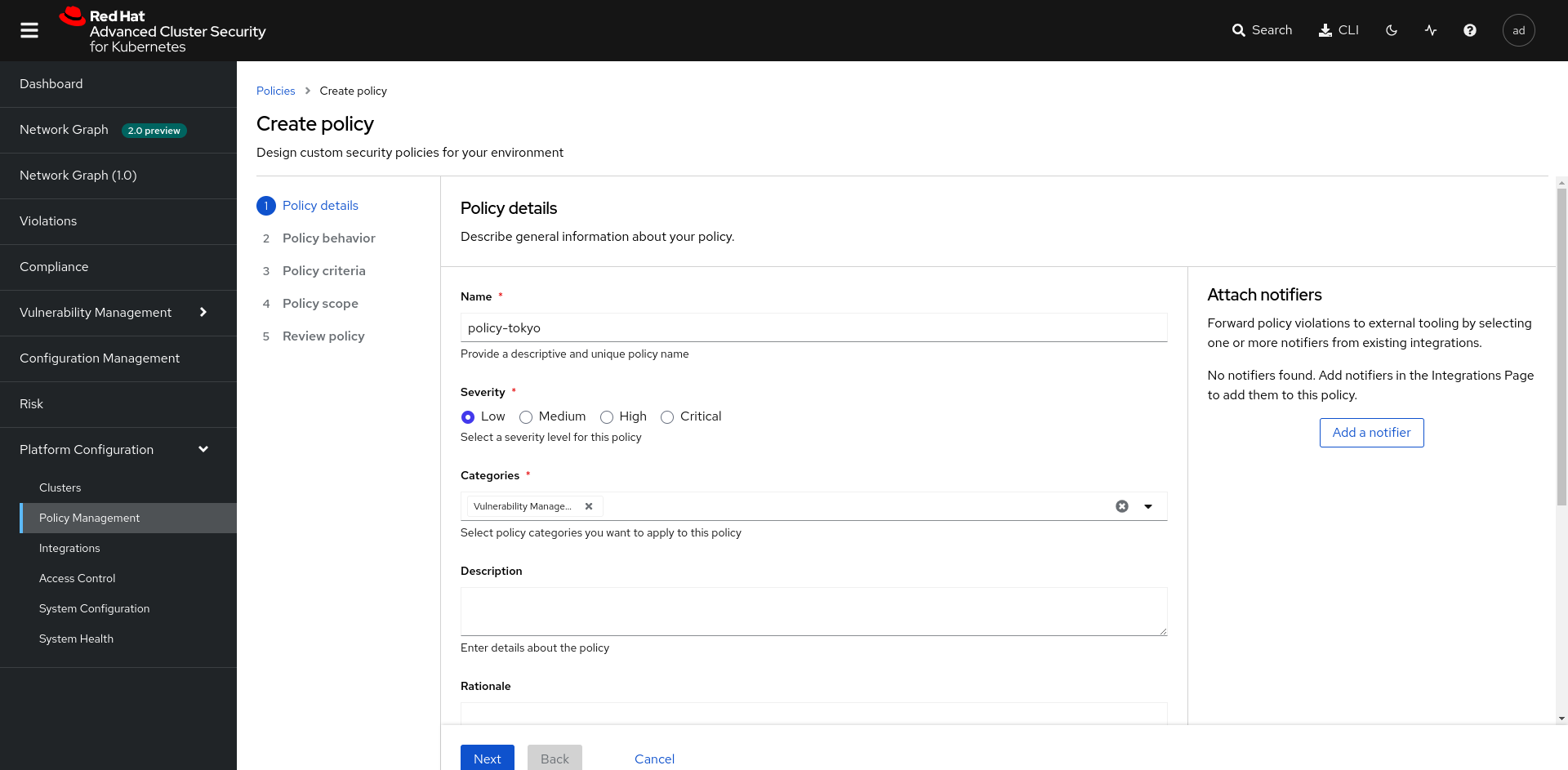
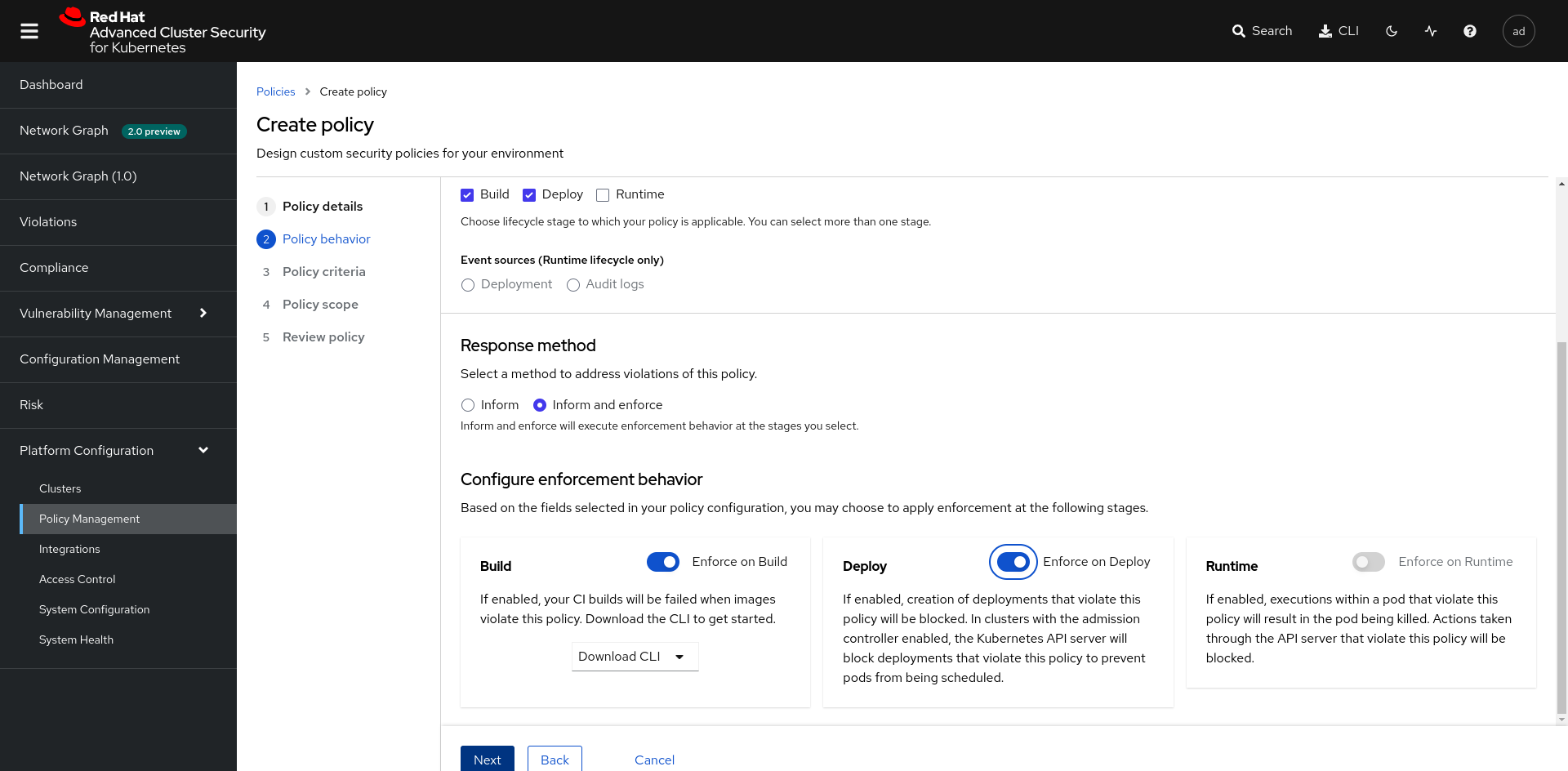
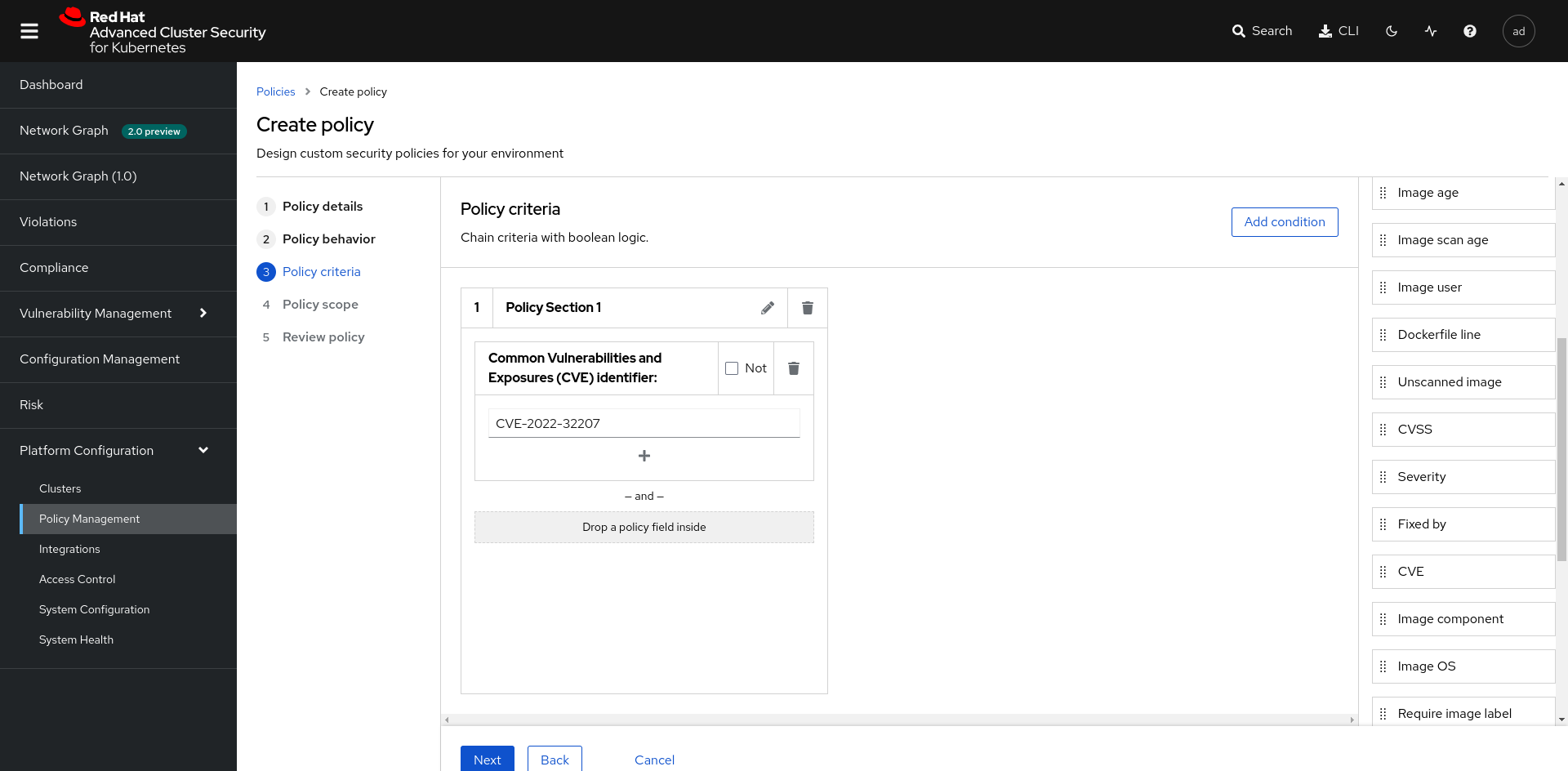
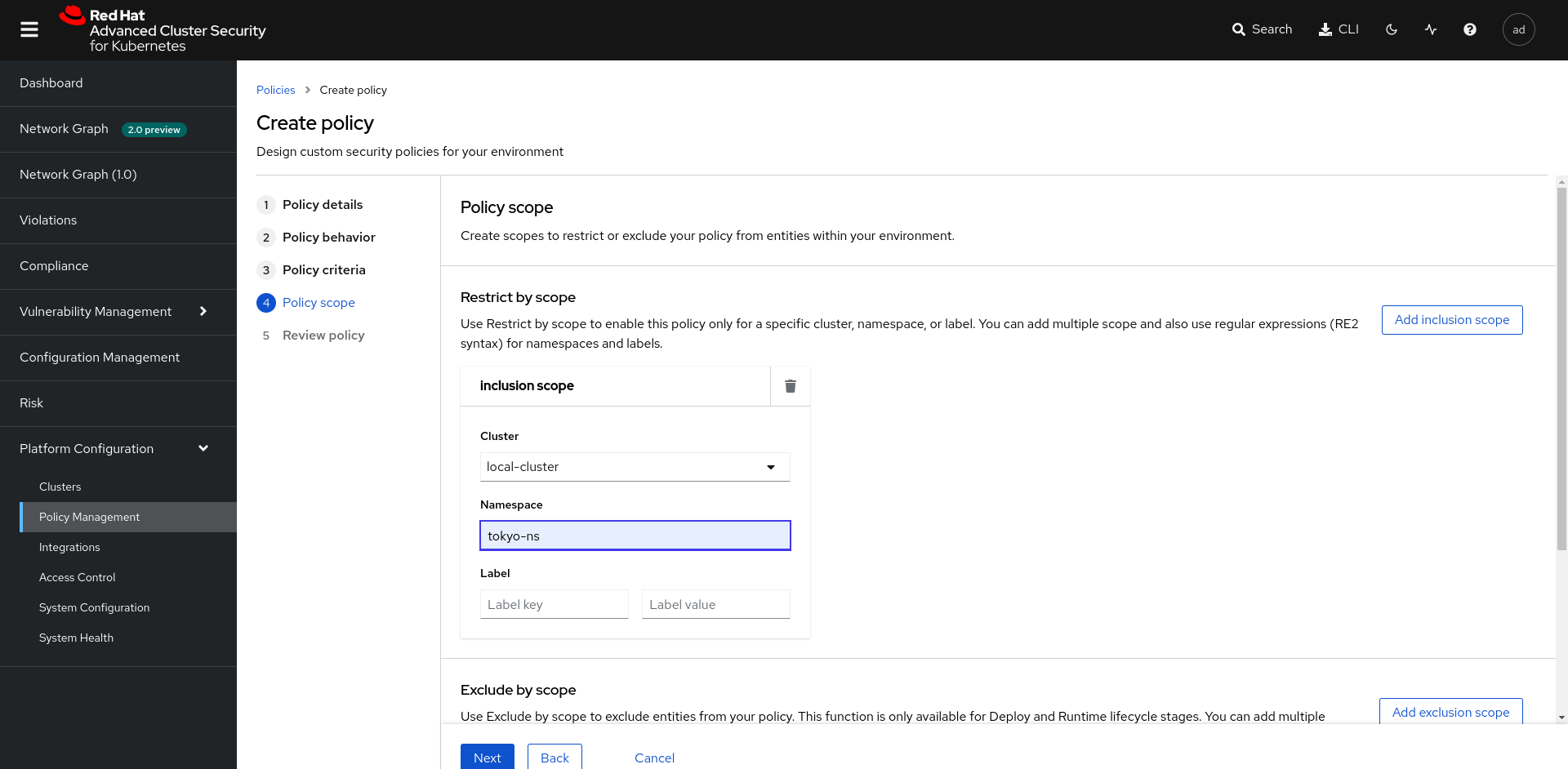
Once this step is completed. Go to Platform Configuration > Policy Management and click Create Policy. You will fill out the form so that all images with the CVE CVE-2022-32207 are blocked during Stage Build and Deploy with an Inform and Enforce method.
The policy must meet the following criterion:
| Parameters | Value |
|---|---|
| Name | policy-<YOUR_CITY> |
| Categories | Vulnerability Management |
| Lifecycle internships | Build and Deploy |
| Response method | Inform and enforce |
| Restrict-by-scope | <YOUR_CITY>-ns |
| Cluster-scope | local-cluster |
| ——— | ——— |